The video "The World of Rails Security" presented by Justin Collins at RailsConf 2015 delves into the essential topic of securing Ruby on Rails applications. As security is often an overlooked area in web development, Collins emphasizes the importance of understanding and implementing security features provided by Rails while also acknowledging its limitations.
Key Points Discussed:
- Overview of Rails Security Features: Collins begins by clarifying that the talk focuses on security mechanisms, not hacking methods. He emphasizes Rails' efforts in providing security against common vulnerabilities.
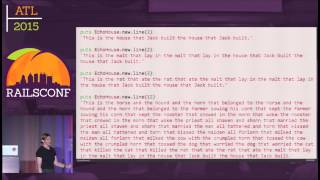
- Cross-Site Scripting (XSS): An explanation of XSS attacks is provided, detailing how malicious scripts can be injected into web pages. The development of automatic escaping in Rails 3 is highlighted as a significant milestone for mitigating XSS vulnerabilities. A historical example, the "perktweet" incident, illustrates the real-world impact of XSS vulnerabilities.
- Cross-Site Request Forgery (CSRF): The risks associated with CSRF are explained, showcasing how Rails employs security tokens in forms to combat this type of attack. Improvements in Rails 4 for easier CSRF protection are also discussed.
- Session Management: The video explains how session management has progressed from signed cookies in earlier Rails versions to encrypted session cookies in Rails 4, enhancing security against session tampering.
- SQL Injection Vulnerabilities: Collins discusses the importance of avoiding SQL injection by using Active Record and warns against passing raw user input directly into query strings.
- Additional Security Challenges: The talk points out areas Rails does not inherently protect against, such as directory traversal attacks and open redirects. Developers must implement their own defensive measures for these vulnerabilities.
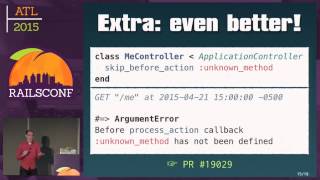
- Static Analysis Tools: Collins identifies a lack of robust static analysis tools for security, encouraging developers to use tools like Brakeman to identify vulnerabilities early in the development cycle.
Conclusions and Takeaways:
- Developers must proactively educate themselves about Rails security features.
- Utilizing existing libraries and static analysis tools are critical steps to improving application security.
- Staying informed about Rails updates is imperative for maintaining application security.
In summary, while Rails offers many built-in security features, it still requires concerted efforts from developers to implement best practices and mitigate vulnerabilities effectively.